Which of the Following Are Parts of the Opsec Process
It involves five steps. Which of the following must be reported.
Operations security OPSEC is a process by which organizations assess and protect public data about themselves that could if properly analyzed and grouped with other data by a.
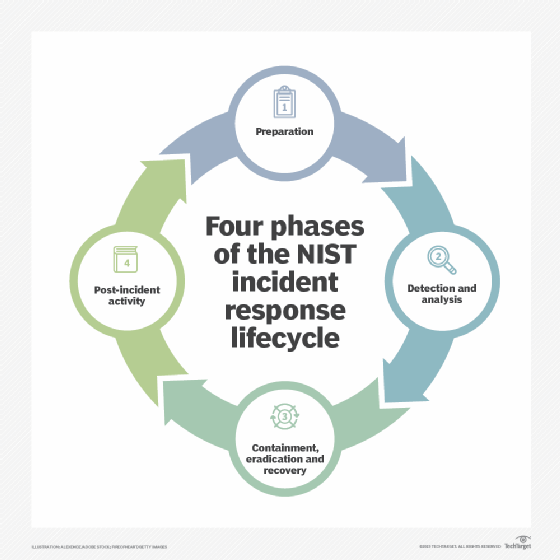
. - Application of appropriate countermeasures. The OPSEC process is most effective when its fully integrated into all planning and operational processes. The OPSEC process includes the following five steps.
Analysis of threats application of appropriate countermeasures conduct vulnerability assessments Most relevant text from all around the web. The OPSEC process involves five steps. Which of the following are parts of the OPSEC process.
Which step in the opsec process requires you to look at your operation through the eyes of an adversary. A critical information list. The OPSEC process has five steps which are as follows.
Each correct answer represents a part of the solution. The last part of the OPSEC process focuses on protecting sensitive information. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures.
Identify your sensitive data including your product research intellectual property financial statements customer information and employee information. The update of OPSEC Coordinator tasks in this manual require no new resources. And an OPSEC support request section.
Analysis of threats Step 2 Deals with identification the adversaries their intent and their capability to use the information against an organization. Log in for more information. The OPSEC process involves five steps.
Once we identify the threats we can study their Techniques Tactics and Procedures TTPs. I dont know the parts of the opsec process. Therefore the identification of critical information would be important to this process because OPSEC would want to protect the critical information first and foremost before attempting to protect any unclassified information.
Identifying critical information identifying the threat assessing vulnerabilities analyzing the risk developing and implementing countermeasures is part of the OPSEC process. OPSEC Process Five Steps - Identification. Answer Which of the following are parts of the OPSEC process.
Identify critical information identify the threat assess vulnerabilities analyze the risk develop and apply countermeasures are parts of the OPSEC process. Add your answer and earn points. The OPSEC process includes the following five steps.
Select all that apply. 1Identification of Critical Information. What are good OPSEC countermeasures.
Answered by wiki 19062021. Updated OPSEC Program self assessment checklist. Which of the following are parts of the OPSEC process.
1 identify critical information 2 identify the threat 3 assess vulnerabilities 4 analyze the risk 5 develop and apply countermeasures. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures. Which of the following are parts of the OPSEC process-Identification of sensitive information-Analysis of threats-Application of appropriate countermeasures-Conduct.
Choose all that apply. The earth rotates around the moon. Identification of system administrators.
1 Minimize predictability from previous operations. The processes involved in operational security can be neatly categorized into five steps. According to Ptolemys model of the movement of celestial bodies A.
- Analysis of vulnerabilities. Which of the following methods may be used to transmit top secret material. Which of the following are parts of the opsec process 1 See answer Advertisement Advertisement CrazyKitty7450 is waiting for your help.
This will be the data you will need to focus your resources on protecting. The OPSEC process involves five steps. See answer 1 Best Answer.
An OPSEC resources section. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures. Display of associated vulnerability components C.
Search for an answer or ask Weegy. Step 1 Identify Critical Information. Which of the following are the process steps of OPSEC.
Which of the following are parts of the opsec process quizlet. A general OPSEC countermeasure strategy should be to. Advertisement Advertisement New questions in Computers and Technology.
Which of the following are part of OPSEC process. 1 identify critical information 2 identify the threat 3 assess vulnerabilities 4 analyze the risk 5 develop and apply countermeasures. The information that youre looking here should be critical to your surroundings and whats going on as well as your intentions abilities activities etc.
Updated OPSEC Activities Annual report. The sun is the center of the universe. Identifying information vitally needed by an adversary which focuses the remainder of the OPSEC process on protecting vital information rather than attempting to protect all classified or sensitive unclassified information.
OPSEC Process. The very first step of the OPSEC process is to identify any information that pertains to the situation youve found yourself in. - Analysis of threats.
Identifying critical information Analyzing threats to that information Examining vulnerabilities to those threats.

What Is Opsec Operations Security

Comments
Post a Comment